Service Mesh: Consul
What is a Service Mesh?
A service mesh is a dedicated layer that provides secure service-to-service communication for on-prem, cloud, or multi-cloud infrastructure. Although service meshes are typically used with a microservice architectural pattern, they are useful in any situation involving complex networking. Their functionalities include traffic control, resiliency, observability and security. Traffic steering is used for content and it allows optimal usage of our resources. Service meshes provide control over chaotic situations (which usually arise in complex networks) along with proper identification and policies to enhance security.
Service meshes can be divided into the control plane and the data plane. The role of the control plane is to secure the mesh, facilitate service discovery, conduct frequent health checks, enforce policies and other operational concerns. Service discovery refers to a central registry of the services and their respective IP addresses. The application needs to be registered on the control plane for it to be able to share with other services how to communicate with it and helps to enforce rules on which service gets to communicate with which other services.
The data plane, on the other hand, handles the communication between services. The amount of knowledge that the services need to have about the network environment is limited by the fact that many service mesh solutions use a sidecar proxy to conduct data plane connections.
What is Consul?
Consul Service Mesh (also known as Consul Connect) provides service-to-service connection authorization and encryption using mutual Transport Layer Security (TLS). Consul is the control plane of the service mesh. Consul can be used with Virtual Machines (VMs), containers, or with container orchestration platforms such as Nomad and Kubernetes. Applications can use sidecar proxies to establish TLS connections for inbound and outbound connections or natively integrate with Connect by using Connect aware SDKs for optimal performance and security.
It is a multi-networking tool that provides a fully functional service mesh solution to address the networking and security issues associated with running cloud infrastructure and microservices. Consul offers a software technique for segmentation and routing. It also offers advantages such as handling failures, retries, and network observability. You can utilize any of these characteristics alone as required or combine them to create a full service mesh and achieve zero trust security.
Architecture
Consul is a distributed system built for a node cluster to operate on. A physical server, cloud instance, virtual machine, or container can all function as a Consul node. The collection of interconnected nodes that Consul runs on is known as a datacenter. Consul supports multiple datacenters and considers this as a common case. It is expected that there will be many clients and three to five servers in a datacenter. This creates a balance between performance and availability in the event of a breakdown because consensus slows down as more machines are added. The number of clients, however, is unlimited and can easily increase to thousands or tens of thousands.
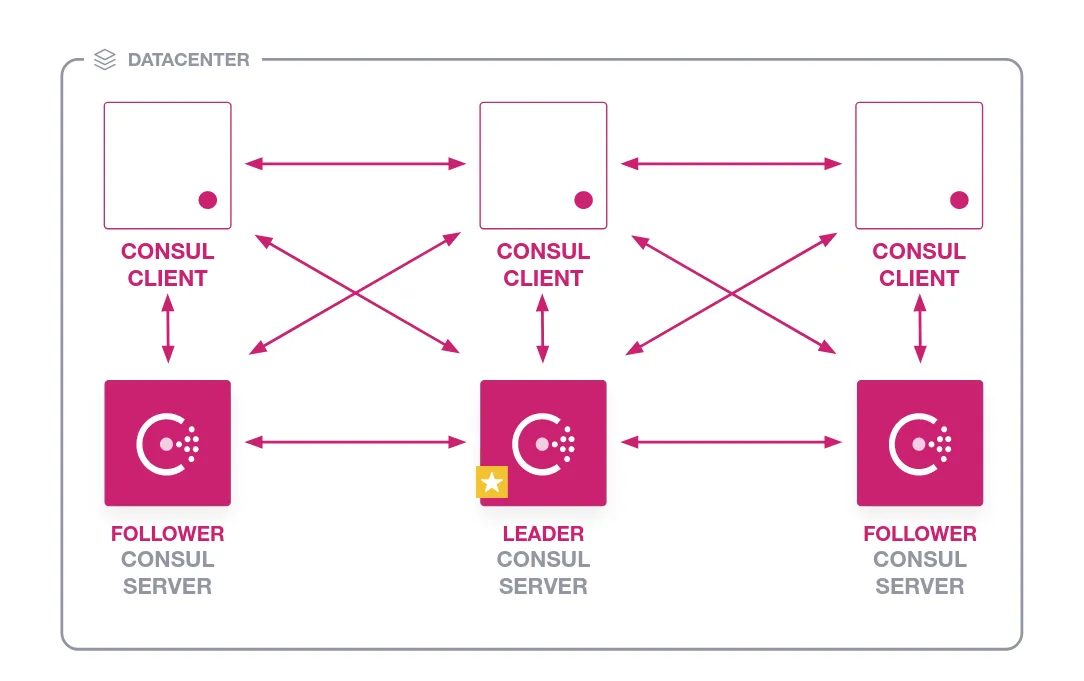
The Consul Agent is responsible for maintaining membership information, registering services, running checks, responding to queries, etc. It is required to run on every node that is a part of the Consul cluster. In some places, client agents may cache data from the servers to make it available locally for performance and reliability. They can either run in server mode or client mode. Client nodes make up for most of the cluster and are lightweight processes. They act as an interface between server nodes for most operations. They run on every node where services are running.
Along with core agent operations, a server node participates in the consensus quorum. The Raft protocol, which offers excellent consistency and availability in the event of failure, serves as the foundation for the quorum. Because they consume more resources than client nodes, server nodes should run on dedicated instances.
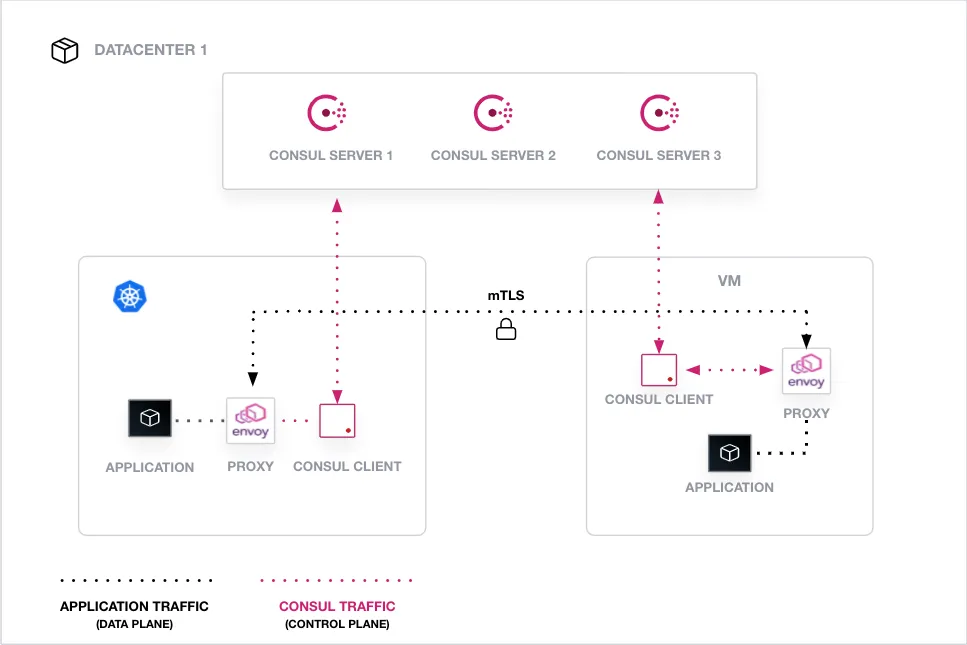
A per-service proxy sidecar manages incoming and outgoing service connections by automatically wrapping and verifying TLS connections. Consul includes its own built-in L4 proxy and has first class support for Envoy. Other than this, we can choose to use any other proxy to plug in as well. The following diagram shows how proxies work:
The lifecycle of a Consul cluster:
- An agent is started.
- An agent joins the cluster.
- Information of the agent is communicated throughout the cluster
- Existing servers will begin replicating to the new node.
Benefits and Compatibility of Consul Connect
New methods of networking are necessary due to the development of cloud infrastructure and microservices designs. There are numerous tools and companies, all of which make different attempts to address the issue. The Consul service mesh solution offers a pure software approach with an emphasis on simplicity and wide compatibility and makes no assumptions about the underlying network.
Consul service mesh streamlines application deployment into a zero-trust network and makes service discovery easier in complex networking situations.
Features of Consul Service Mesh:
- Service Discovery
Consul provides a service catalog, configurable service routing, health checks, automatic load balancing, and geo-failover across multiple instances of the same service. The capacity to control changes in the service landscape of your network becomes essential when new versions of a service are introduced and must coexist with existing instances of the same application, frequently running on different versions. The agent provides a simple service definition format to declare the availability of a service and to potentially associate it with a health check.
- Zero-trust Security Model
Trust can be exploited and with the increasing number of services, there are higher chances of breach. The Consul service mesh control plane can be configured to enforce mutual TLS (mTLS), and will automatically generate and distribute the TLS certificates for every service in the mesh. The certificates are used for both service identity verification and communication encryption.
- Simplify Application Security with Intentions
Communication between services is secure within the mesh once the service sidecar proxies have been set up. To designate which services are permitted to communicate with one another, you might want to build a more granular set of policies. Consul Intentions are used to limit which services can make requests or create connections and define access control for services through Connect. We can manage intentions via the UI, CLI, or API. The proxy or a natively integrated application enforces intentions on inbound connections or requests.
Compatibility of Consul Connect:
- First-Class Kubernetes Support
By offering an official Helm chart for installing, configuring, and upgrading Consul on Kubernetes, Consul enables first-class Kubernetes support. The chart automates Kubernetes's Consul service mesh installation and configuration.
- Platform Agnostic and Multi-Cluster Mesh
Consul works with all cloud providers and architectures. You can expand the scope of your Kubernetes clusters to include services that aren't run using Kubernetes by using the service catalog sync and auto-join features. In order to facilitate safe service-to-service communication between Nomad tasks and jobs, Consul additionally interfaces with HashiCorp Nomad.
