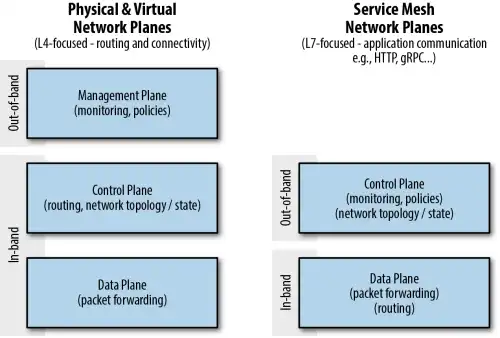
Network Planes
Learn more about service mesh fundamentals in The Enterprise Path to Service Mesh Archictures (2nd Edition) - free book and excellent resource which addresses how to evaluate your organization’s readiness, provides factors to consider when building new applications and converting existing applications to best take advantage of a service mesh, and offers insight on deployment architectures used to get you there.
Data Plane
Service proxies (gateways) are elements of the data plane. The number of proxies present depends on the number of services you’re running and the design of the service mesh’s deployment model. Some service mesh initiatives create their own proxies, while others rely on existing ones. Envoy is a popular choice as the data plane element.
BFEBFE is a Golang-based modern proxy. HTTP, HTTPS, SPDY, HTTP2, WebSocket, TLS, and FastCGI are among the load balancing algorithms and multiple protocols it supports. Users can configure rule and content-based routing using BFE's own domain-specific language.
EnvoyEnvoy is a modern proxy developed in C++. Envoy's initial success stemmed from its ability to hot-reload both its configuration and itself (update itself in place while handling connections). API gateways, ingress controllers, service meshes, and managed offerings by Cloud providers are just a few of the projects that have been built on top of Envoy. Istio, App Mesh, Kuma, Open Service Mesh, and other service meshes (discussed in the Control Plane section) have been built on top of Envoy.
Linkerdv2The linkerd2-proxy is explicitly built for the service mesh sidecar use case, Linkerd, can be significantly smaller and faster than Envoy-based service meshes. Rust was chosen as the implementation language because it is memory-safe and highly performant. This service proxy purports a sub-1ms p99 traffic latency. Open-source. From Buoyant.
NGINXnginMesh project deploys NGINX as a sidecar proxy in Istio. Open source. Written primarily in C and Rust. From NGINX.
The following are a couple of early, and now antiquated, service mesh–like projects, forming control planes around existing load-balancers:
SmartStackComprising two components: Nerve for health-checking and Synapse for service discovery. Open source. From AirBnB. Written in Ruby.
NelsonTakes advantage of integrations with Envoy, Prometheus, Vault, and Nomad to provide Git-centric, developer-driven deployments with automated build-and-release workflow. Open source. From Verizon Labs. Written in Scala.
Control Plane
ConsulAnnounced service mesh capable intention in v1.5. Became a full service mesh in v1.8. Consul uses Envoy as its dataplane, offering multi-cluster federation. Open and closed source. From HashiCorp. Primarily written in Go.
LinkerdLinkerd is hosted by the Cloud Native Computing Foundation (CNCF) and has undergone two major releases with significant architectural changes and an entirely different code base used between the two versions.
Linkerdv1The first version of Linkerd was built on top of Twitter Finagle. Pronounced “linker-dee”, it includes both a proxying data plane and control plane, Namerd (“namer-dee”), all in one package. Open source. Written primarily in Scala.
The second major version of Linkerd is based on a project formerly known as Conduit, a Kubernetes-native and Kubernetes-only service mesh announced as a project in December 2017. In contrast to Istio and in learning from Linkerdv1, Linkerdv2’s design principles revolve around a minimalist architecture and zero configuration philosophy, optimizing for streamlined setup.
Announced as a project in May 2017, Istio is considered to be a “second explosion after Kubernetes” given its architecture and surface area of functional aspiration.
NGINX Service Mesh is a more recent arrival into the service mesh arena, having released in September 2020. Using an Nginx Plus augmented to interface with Kubernetes natively as its dataplane, supports ingress and egress gateways through NGINX Plus Kubernetes Ingress Controllers. NGINX Service Mesh offers its control plane as a CLI, meshctl, using the Service Mesh Interface (SMI) specification as its API. Both Open and closed source. From NGINX. Primarily written in C.
Others including Open Service Mesh, Maesh, Kuma, App Mesh...This list is meant to give you an idea of the wide range of service meshes that are currently available. A complete list of service meshes and their details may be found in the Layer5 service mesh landscape, maintained by the community.
Management Plane
The management plane sits a level above the control plane. It can perform various tasks such as operational patterns, business system integration, and application logic enhancement while functioning across different service meshes. A management plane can perform workload and mesh configuration validation, whether in preparation for onboarding a workload into the mesh or as you upgrade to new versions of components running your control and data planes or new versions of your applications. Management planes help organizations running a service mesh get the most out of their investment. Performance management is one part of maintaining service meshes, a function at which Meshery excels.
Mesherythe cloud native management plane for adopting, operating and developing on different service meshes. Meshery integrates business processes and application logic into service meshes by deploying custom WebAssembly (WASM) modules as filters in Envoy-based data planes. It provides governance, policy and performance and configuration management of service meshes with a visual topology for designing service mesh deployments and managing the fine-grained traffic control of a service mesh. - Open source. Created by Layer5. Primarily written in Go.
As the lingua franca of the cloud-native ecosystem, Go is certainly prevalent and you might expect most projects to be written in Go. By the nature of their task, data planes must be highly efficient in the interception, introspection, and rewriting of network traffic. As a data plane component, Envoy is written in C++11 because it provides excellent performance (surprisingly, some say it provides a great developer experience). Rust has found its way into service meshes as a growing language (and something of a C++ competitor). Because of its properties around efficiency (outperforming Go) and memory safety (when written to be so) without garbage collection, Rust has been used for Linkerdv2’s data plane component, for the former nginMesh’s Mixer module (see “How to customize an Istio service mesh”), and is now being used in WebAssembly programs as data plane filters (see “Write WASM filters for Envoy in Rust and deploy with Consul”).
